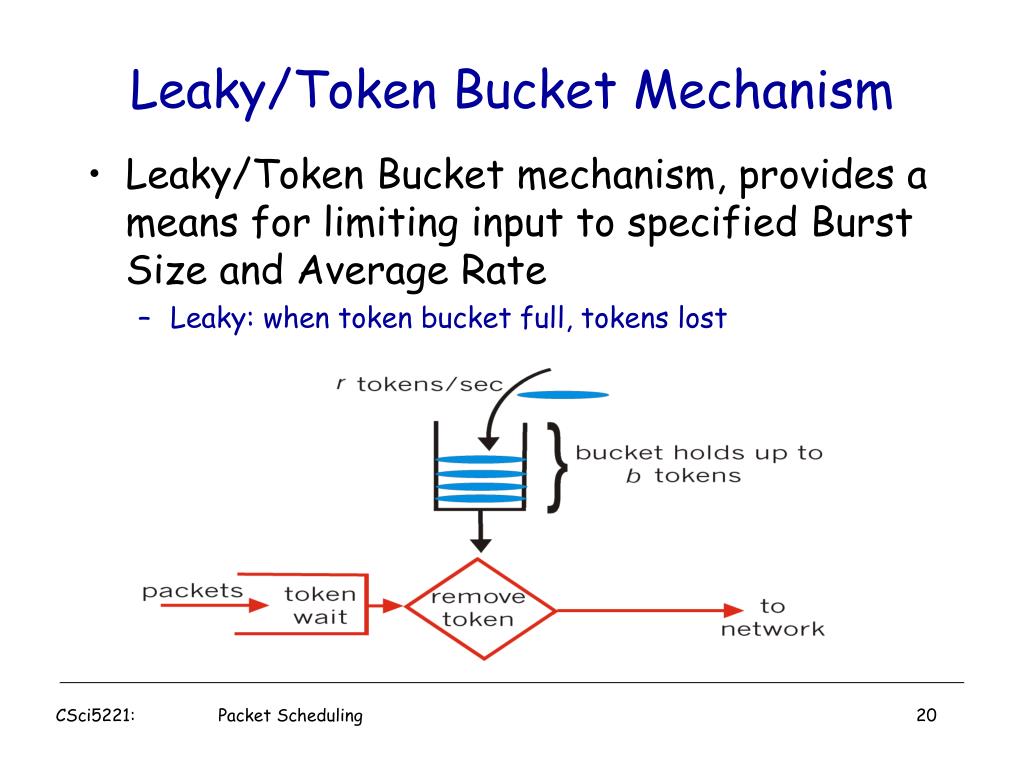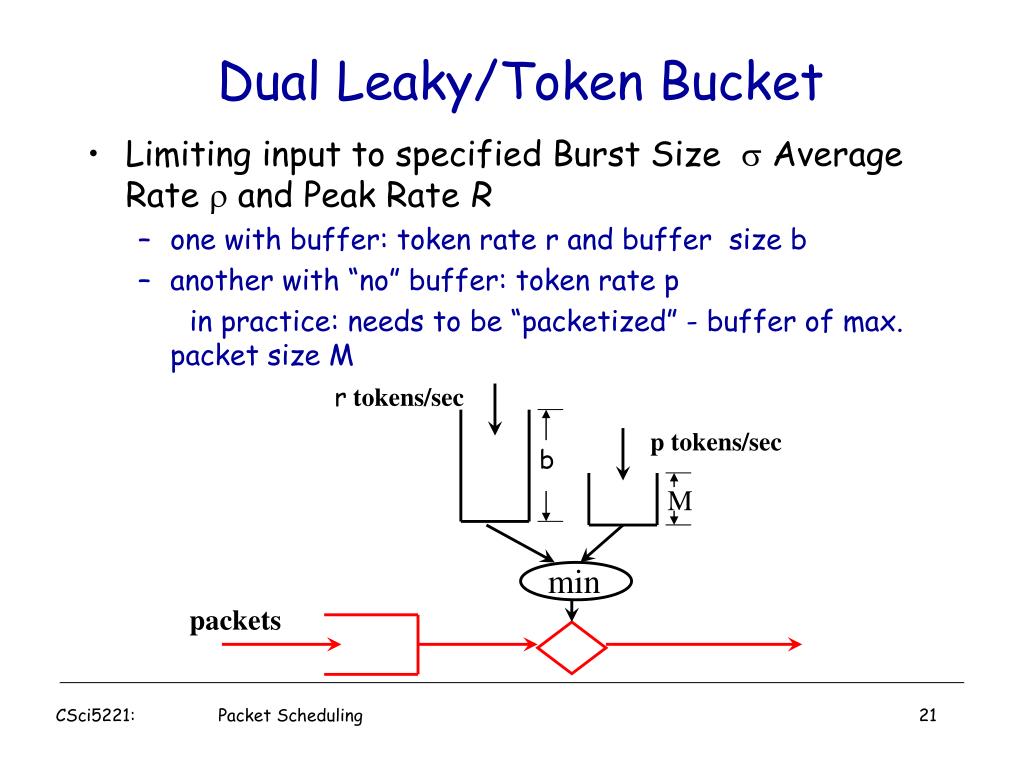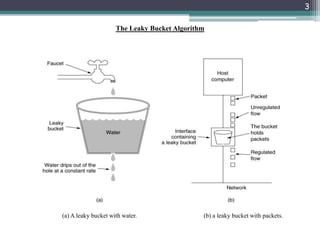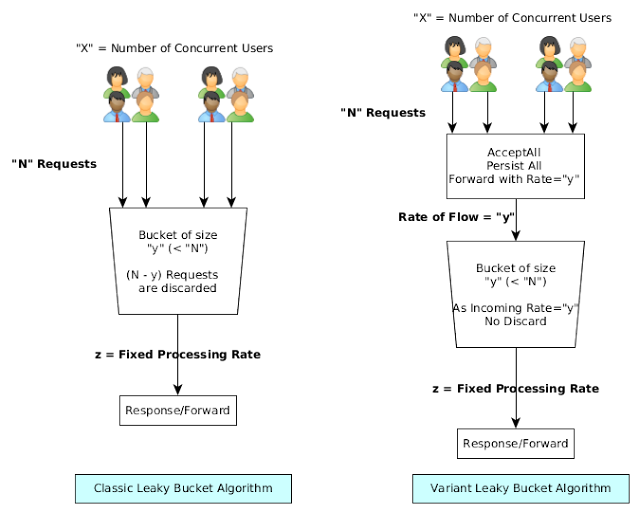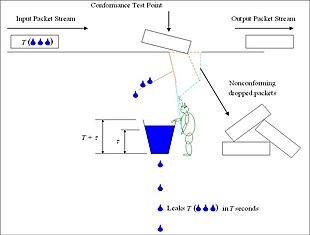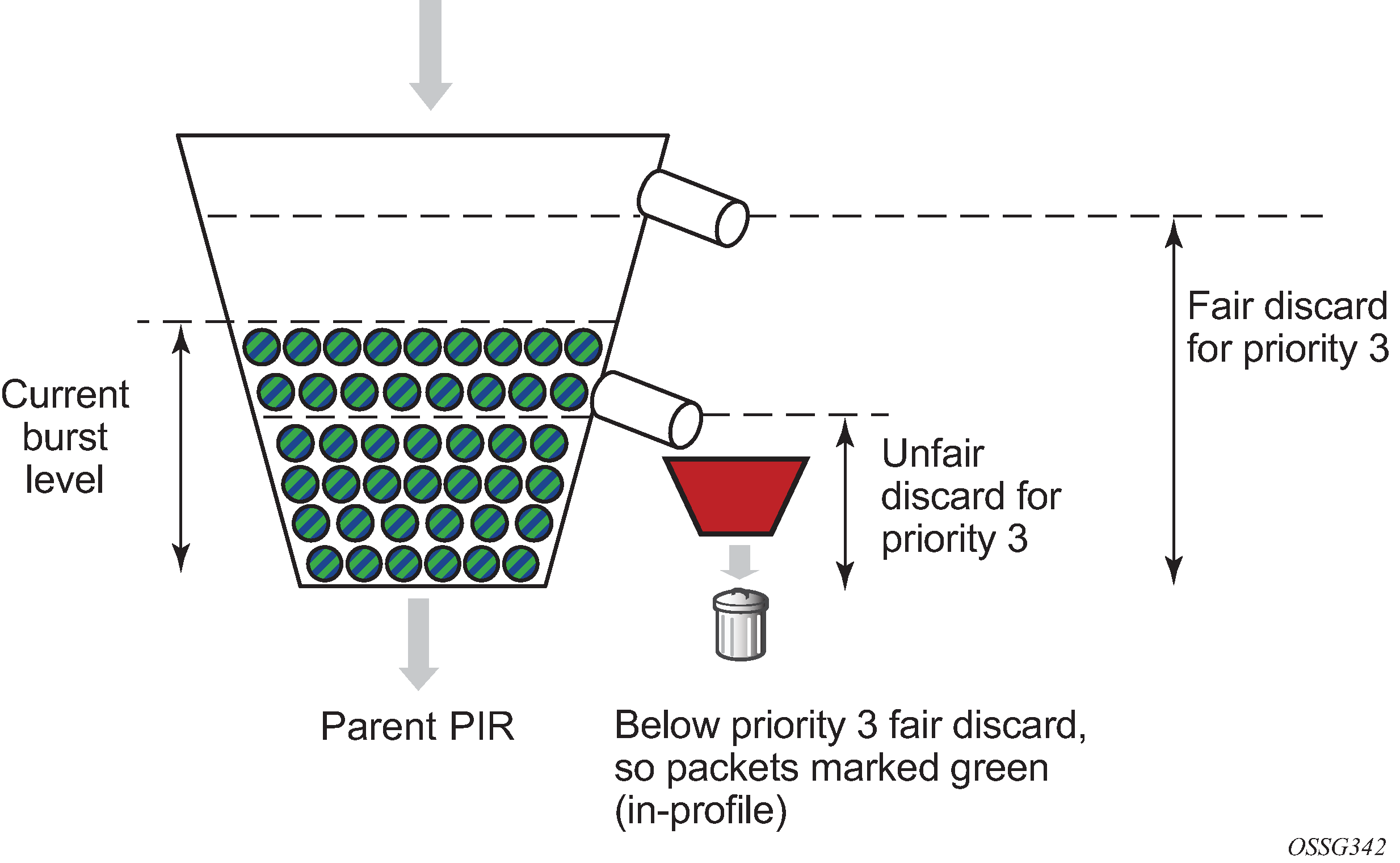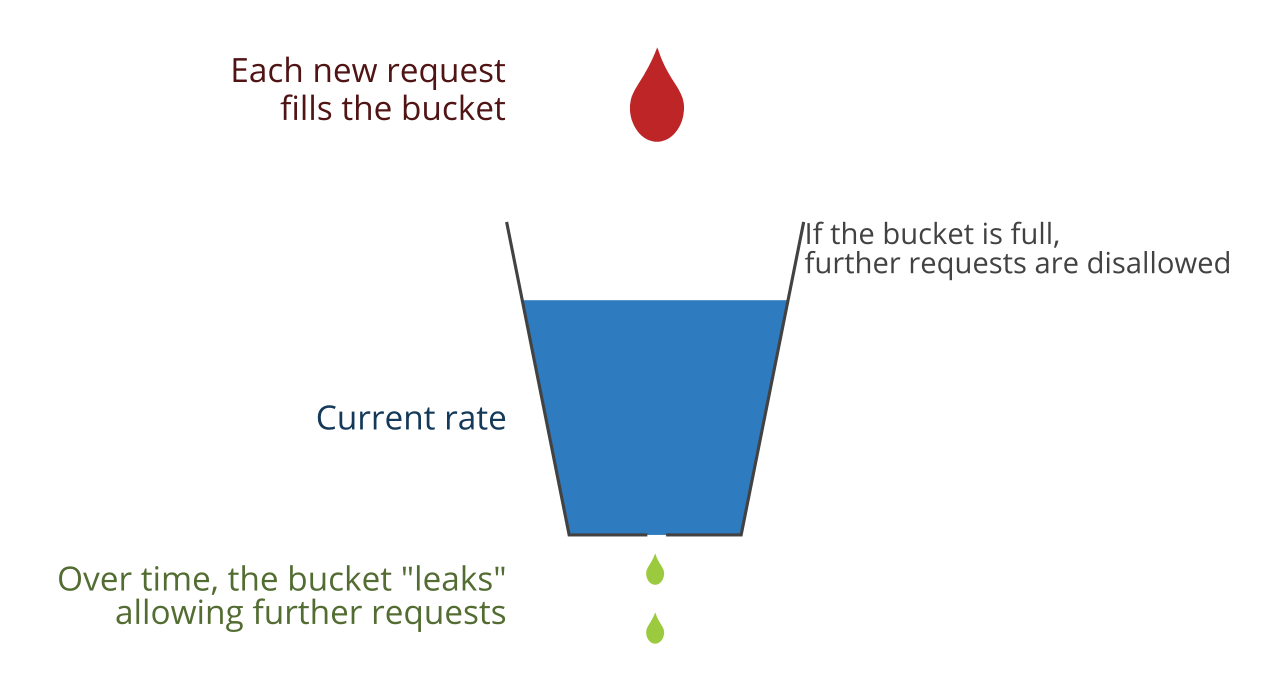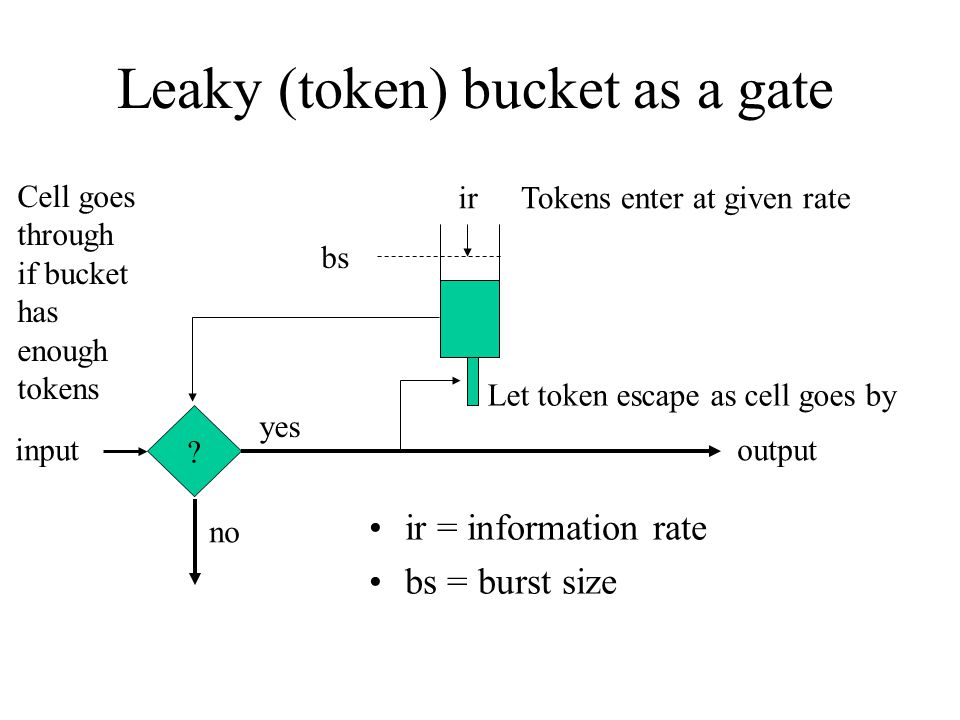
CS 4594 Broadband ATM GCRA and Leaky Bucket. From the ATM Forum The GCRA is used to define conformance to the traffic contract. For each cell that arrives. - ppt download
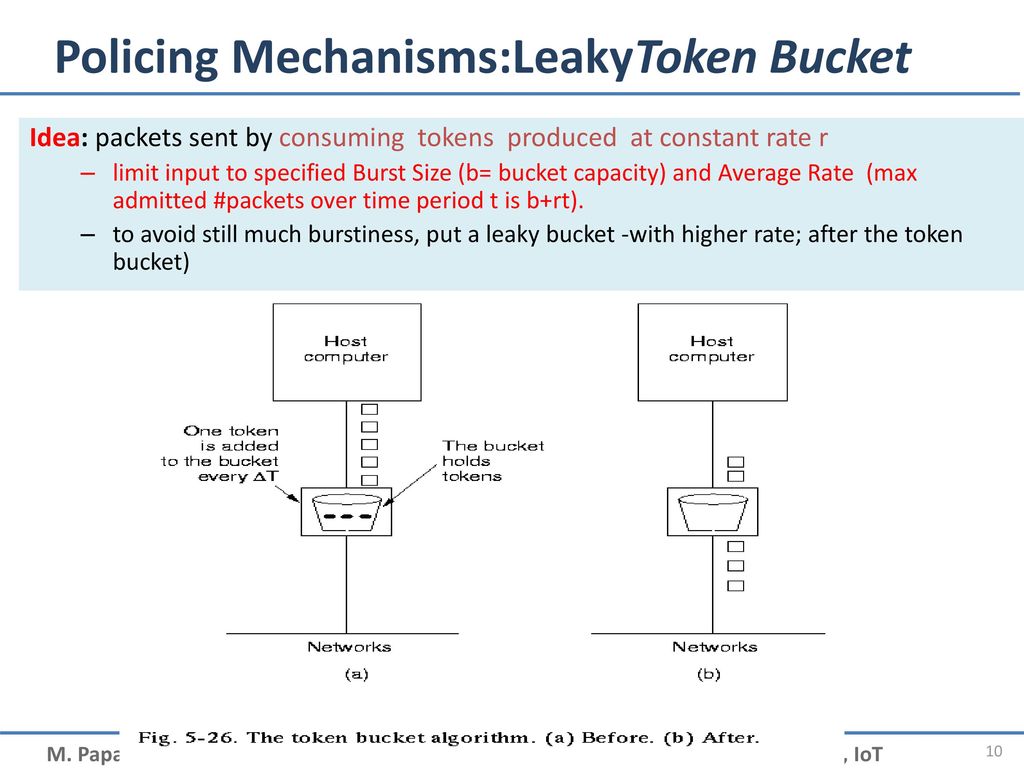
Course on Computer Communication and Networks Lecture 12 Continuously evolving Internet-working Part 2: QoS, traffic engineering, SDN, IoT EDA344/DIT. - ppt download
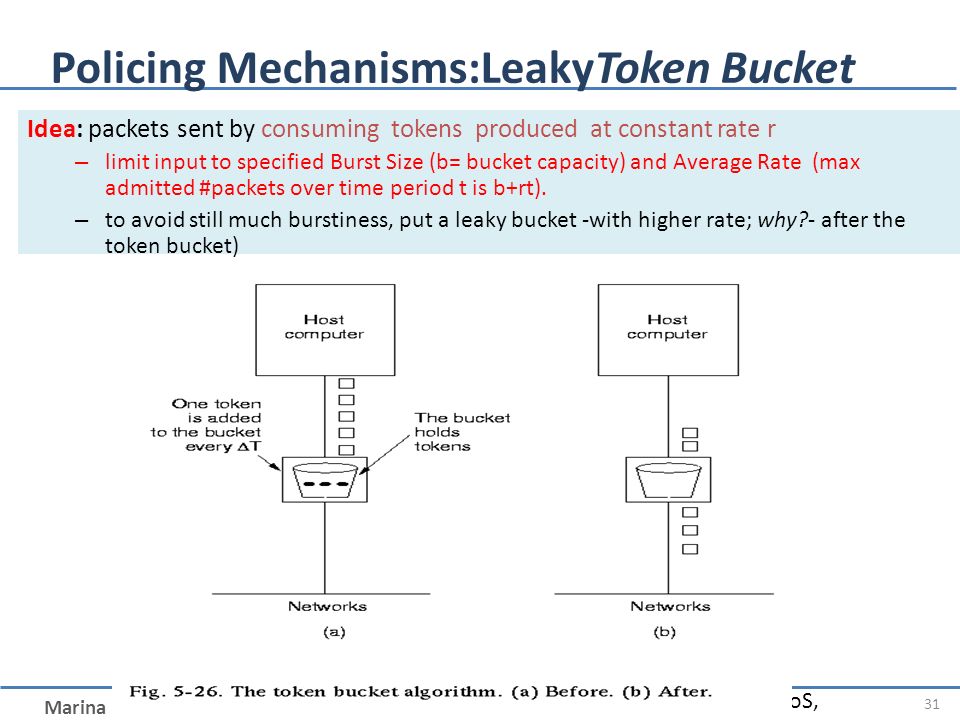
Course on Computer Communication and Networks Lecture 13 Chapter 7: Multimedia networking Chapter 3-5: VC-type congestion control EDA344/DIT 420, CTH/GU. - ppt download